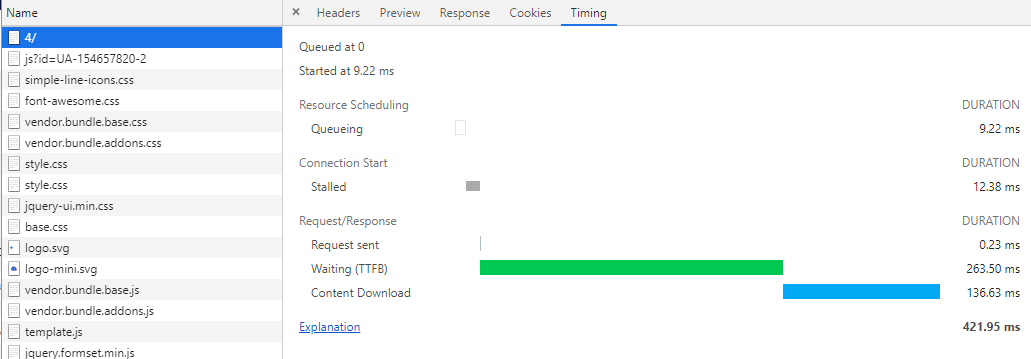
I’ve undertaken a hobby project over the last several months to build a Django web application. I have in mind to build a budgeting or…
There are only a handful of things in this world I’m certain have a lasting impact on ourselves and our world. Our Relationships with Our…
Recently I’ve been working on moving a common web application hosted in a LAMP stack from an Ubuntu box I’d like to retire to CentOS…
One of my recent projects was to customize the appearance of the Active Directory Federation Services (AD FS) 3.0 sign-in page to give it a…
I have come to the conclusion that science projects aren’t for the student still in school. They are in fact the public education system’s way…